Smart home technology is now a standard amenity in rental housing properties nationwide. Renters love the convenience. Property managers love the control. Property values increase, and everyone saves time and money. However, one topic still remains of concern to every smart home technology user — security. The benefits of digital property access and remote property management are well known, but so too are the risks. Proptech security breaches can lead to unauthorized property access, data privacy violations, and rental scams. To minimize these risks, proptech providers must implement robust security measures throughout their product solutions and across their operations. Both renters and property managers must have confidence that their data and assets are protected at all times. At Rently, we prioritized security considerations early in our product development. Rently’s security features overlay our entire system architecture, traverse all of our operations, and extend outwards to protect managers’ platforms and renters’ data.

Tier 1: A Secure System Architecture
Rently has implemented high-grade security protocols across all of our smart home devices, network gateways, management software platforms, and mobile apps. In addition, we encrypt and secure all of the commands and data transiting our network.
By using this multi-layer, cross-functional approach, the Rently System Architecture ensures “point-to-point” security. Ultimately, all of these secure network points mesh to create an “end-to-end” security framework in which every communication between a user and a device is authenticated and encrypted.

Network Security
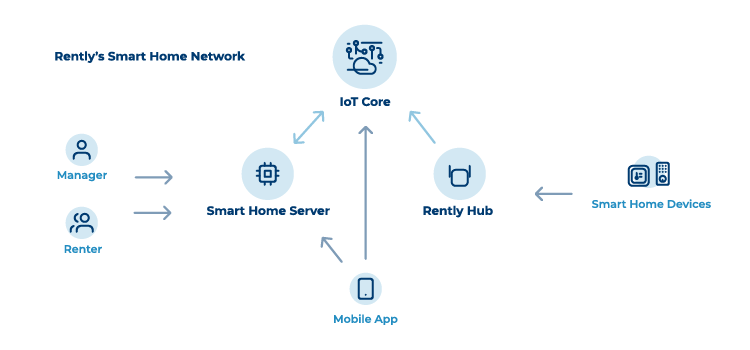
Rently’s Smart Home Network has 3 main components: a Smart Home Server, an IoT (“Internet of Things”) Core, and a Hub.
Rently’s Smart Home Server (SHS) is a relational database that processes requests from the Web and mobile apps. Our server utilizes Amazon Web Services’ (AWS) Cognito™ and IAM™ (Identity and Access Management) software to provide a sophisticated multi-layer, rules-based, access control system for properties and devices.
All data stored in the Rently server is encrypted and is protected by AWS Shield™, a web application firewall that defends against the most frequently occurring denial of service attacks. In addition, Rently has added Amazon Cloudfront™ and Route 53™ to protect against (Layer 3 and 4) infrastructure attacks.
Next, Rently’s IoT Core ensures the secure interaction between our smart home devices and our managed AWS cloud service. The IoT Core has the capability to support millions of devices and securely route billions of messages to any Rently device endpoint, all according to proprietary Rently rules engines.
Finally, Rently’s Hub maintains consistent Internet connections between our IoT Core and our smart home devices. Our Hub runs the Linux Operating System, which has a proven track record of security and stability. The Rently Hub can send out security patches remotely, on demand. All of the connections initiated by the Rently Hub between smart home devices and our server are authenticated with the x.509 client certification process.
Device Security
Every smart home device must be both physically and digitally secure. In addition, there must be overlapping security between the physical and digital architectures.
On the physical level, Rently works with Kwikset™ and Yale™, top-tier lock manufacturers, who have achieved industry standard certifications from the Builders Hardware Manufacturers Association (BHMA). These smart locks offer tamper-resistant materials and alarms that sound if someone enters an incorrect access code more than 3 times. Kwikset’s SmartKey Security™ is resistant to kick-ins, picks bumps, drills, and saws.
On the digital level, all communications between devices and our server use the Z-wave security protocol for encryption, which has demonstrated access device security for more than a decade.
All devices that connect to the Rently network are secured to the highest standard, whether or not they are connected to our main cloud server.

Data Security
Rently encrypts all data, whether in transit or at rest.
In transit, Rently sends data with Transport Layer Security (TLS) that uses HTTPS, MQTT and WebSocket protocols that always choose the highest level of security as their default settings.
High-energy servers send data at a high encryption level (AES-256) and low-energy devices send data at a lower encryption level (AES-128), however all data is encrypted.
In addition, when a Rently smart home hub communicates with Rently’s IoT Core, each endpoint of the communication runs over the Public Key Infrastructure (PKI), an industry-standard system that assigns encrypted digital certificates to validate account identities. (These encrypted certificates are stored locally on the device.)
At rest, all Rently user and device data is stored in the encrypted version of AWS’ Dynamo™ database. As an additional layer of security, Rently data lives in an encrypted table within that database.
Keys to the data in the Rently Dynamo™ database are encrypted and located in the AWS Key Management Service. AWS’ Cloudtrail™ monitors and audits the Rently databases and related services on an ongoing basis, in real-time, and sends out alerts for any security breach.

Industry Certifications
Security challenges are always evolving and it’s important for proptech providers to keep up with emerging threats.
Rently trains our engineers in best practice security protocols before they start coding and building applications for clients, and they receive ongoing updates about how to keep information secure.
We also commission regular systems testing by external security experts and promptly addresses any vulnerabilities.
Rently has achieved the following industry-recognized security certifications:
ISO/IEC 27001:2013 Certification of Information Security Management System which establishes policies and procedures related to the legal, physical, and technical control of information.
ISO/IEC 27701:2019 Privacy Information Management System which establishes policies for managing personal data and ensures a strong technical integration point between data security and data privacy.
SOC2 (Types 1&2), a rigorous audit that ensures that a company has the highest level of operational security controls in place to safeguard user and operator data.
Rently’s security certifications cover all office locations and key departments in our organization, including research and development, engineering, product, customer support, operations, human resources, accounting, IT, sales, and client success.

Tier 2: A Secure Management Platform
After having created a secure system architecture, the next step Rently focused on was to create security features for managers using our technology.
Beginning already at the listing phase of leasing, Rently offers property managers the ability to watermark their property photos so they cannot be lifted from Internet listing sites. This prevents others from posting these photos and pretending to manage the property, in order to collect fees from unsuspecting renters.

Another way that Rently helps managers address security issues is by installing smart home devices onto their properties to protect their assets while automating leasing tasks.
For instance, Rently’s smart locks enable self-guided tours, which are growing in popularity among renters. In fact, 84% of renters would prefer to schedule a self-guided tour and view a property outside of regular business hours.
Property managers recognize the increased demand for self-guided tours. However, they also know that they must protect their assets and avoid rental prospects with ulterior motives.
To help managers address their concerns, Rently’s self-guided tour solution incorporates security checks at multiple points in the touring process.
First, rental prospects must register for tours online with their name, email, and phone number. Then they must also provide a credit card number as another layer of identity verification.
Next, at the property itself, the same prospect is required to provide a photo of a valid ID and a matching selfie photo from their smartphone. Rently uses sophisticated facial recognition software to verify that the person taking the tour is the same person who registered for the tour.
During the tour, Rently’s smart home sensors provide managers with real-time alerts if unauthorized movement occurs within the property.
Later, Rently provides property managers with real time notifications that a renter completed their tour.
Rently’s Manager Portal allows for real-time monitoring of tours and allows managers to stay in total control of property access at all times.
For additional information about how Rently helps prevent rental scams, please click here.
Tier 3: A Secure Mobile App
A secure mobile app (for renters and managers) completes Rently’s smart home technology ecosystem.
In order to ensure renters’ data privacy, Rently uses Amazon Cognito™ to protect and manage user information from mobile and web applications.
Additionally, to ensure managers’ control over property access, Rently’s mobile app has digital gateways that authenticate users and approve property access.
The Rently App authenticates users – whether renter or manager – by using strong passwords and biometric data, such as FaceID and Fingerprint. All user authentication data is stored locally on the platform upon which the Rently App operates. So, for instance, using an iPhone, a user’s unique data is stored in their own iPhone’s secure vault.
Next, Rently’s App has security controls for unlocking a door from a mobile device. When a user first logs in to our app, their account must be verified. Only then can a user activate the “unlock” button, which initiates encrypted commands between Rently’s Server and the IoT Core, permitting the digital unlocking of the physical lock.
Although not initiated by the user, another security feature of Rently’s App is its notification feature. Managers and residents will receive immediate alerts to their mobile devices if a door or window has been opened or if motion is detected.
Conclusion
No matter how beneficial a proptech solution might be to managers and renters, none of those benefits matter if the technology is not secure.
As the digital world becomes increasingly complex, mobile, and closely connected to our homes, solution providers must be vigilant to maintain the highest possible standards for security.
Rently has taken great care to build robust security features into every layer of our smart home solution.
We want renters to know that their information is safe when they schedule self-tours with us, and we want managers to feel confident that their property is protected at all times.
For us, truly smart homes are also secure homes.